- Home
- Mobiles
- Mobiles News
- iPhone Flaw Can Reportedly Be Exploited to Automatically Make Calls
iPhone Flaw Can Reportedly Be Exploited to Automatically Make Calls
By NDTV Correspondent | Updated: 25 August 2014 12:48 IST
Click Here to Add Gadgets360 As A Trusted Source

Advertisement
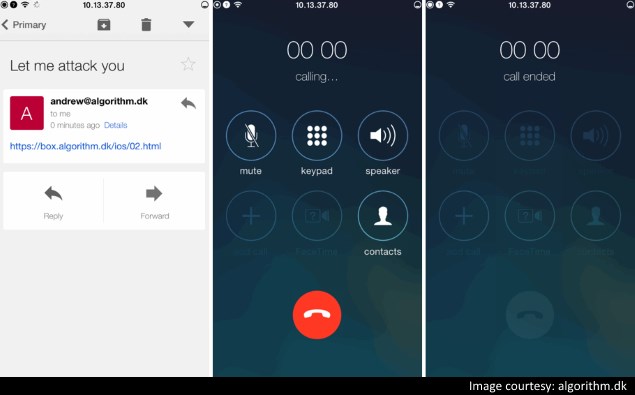
A potential flaw in the way Apple makes life easier for users and app developers could be exploited to force devices to automatically make premium calls, inflating the phone bills of victims and, in some cases, stealing their identities.
Apple allows apps to make phone calls when a user taps a number on screen, by identifying actionable text with tags called URIs (Uniform Resource Identifiers). Calls can be placed without a confirmation dialog popping up when the scheme is used within apps. Such functionality was designed for search and listings apps. However, it has also been used for messaging and communications apps, such that when a person sends someone else a phone number, the recipient can tap it to call it.
Security researcher Andrei Neculaesei has now demonstrated that attackers can abuse the "tel:" URI scheme by packaging JavaScript along with the target URI which automatically executes the call without waiting for a user to tap anything. With no an OS-level warning in place, an attacker could force phones to dial premium numbers which are instantly picked up on the receiving end, and collect money which would be charged to the victims' phone bills.
An attacker would only have to send out spam messages with a disguised URL to the manipulated code for the scheme to work. In a post to his website, reported by Engadget, Neculaesei demonstrates the flaw at work in the Facebook Messenger, Gmail and Google+ apps running on an iPhone. Dozens of similar apps might be similarly vulnerable
Rather than blame Apple exclusively, Neculaesei blames the app developers for using the tel: URI irresponsibly. The exact design of the scheme is documented by Apple, and an alternative which forces a prompt, telprompt:, also exists. Apple's URI implementation is meant to give app developers options so that users are not inconvenienced by confirmation dialogs for every call they try to place through an app's interface.
The feature (or bug) takes on a more serious tone when used to trigger FaceTime calls. Users could be tricked into placing video calls which are picked up instantly, at which point screenshots of their faces could be saved without their knowledge.
While the problem is not the result of a traditional security flaw or bug, Apple could force prompts in all cases to mitigate the issue, although this would annoy users.
Apple allows apps to make phone calls when a user taps a number on screen, by identifying actionable text with tags called URIs (Uniform Resource Identifiers). Calls can be placed without a confirmation dialog popping up when the scheme is used within apps. Such functionality was designed for search and listings apps. However, it has also been used for messaging and communications apps, such that when a person sends someone else a phone number, the recipient can tap it to call it.
Security researcher Andrei Neculaesei has now demonstrated that attackers can abuse the "tel:" URI scheme by packaging JavaScript along with the target URI which automatically executes the call without waiting for a user to tap anything. With no an OS-level warning in place, an attacker could force phones to dial premium numbers which are instantly picked up on the receiving end, and collect money which would be charged to the victims' phone bills.
An attacker would only have to send out spam messages with a disguised URL to the manipulated code for the scheme to work. In a post to his website, reported by Engadget, Neculaesei demonstrates the flaw at work in the Facebook Messenger, Gmail and Google+ apps running on an iPhone. Dozens of similar apps might be similarly vulnerable
Rather than blame Apple exclusively, Neculaesei blames the app developers for using the tel: URI irresponsibly. The exact design of the scheme is documented by Apple, and an alternative which forces a prompt, telprompt:, also exists. Apple's URI implementation is meant to give app developers options so that users are not inconvenienced by confirmation dialogs for every call they try to place through an app's interface.
The feature (or bug) takes on a more serious tone when used to trigger FaceTime calls. Users could be tricked into placing video calls which are picked up instantly, at which point screenshots of their faces could be saved without their knowledge.
While the problem is not the result of a traditional security flaw or bug, Apple could force prompts in all cases to mitigate the issue, although this would annoy users.
Comments
Get your daily dose of tech news, reviews, and insights, in under 80 characters on Gadgets 360 Turbo. Connect with fellow tech lovers on our Forum. Follow us on X, Facebook, WhatsApp, Threads and Google News for instant updates. Catch all the action on our YouTube channel.
Related Stories
Popular on Gadgets
- Samsung Galaxy Unpacked 2026
- iPhone 17 Pro Max
- ChatGPT
- iOS 26
- Laptop Under 50000
- Smartwatch Under 10000
- Apple Vision Pro
- Oneplus 12
- OnePlus Nord CE 3 Lite 5G
- iPhone 13
- Xiaomi 14 Pro
- Oppo Find N3
- Tecno Spark Go (2023)
- Realme V30
- Best Phones Under 25000
- Samsung Galaxy S24 Series
- Cryptocurrency
- iQoo 12
- Samsung Galaxy S24 Ultra
- Giottus
- Samsung Galaxy Z Flip 5
- Apple 'Scary Fast'
- Housefull 5
- GoPro Hero 12 Black Review
- Invincible Season 2
- JioGlass
- HD Ready TV
- Latest Mobile Phones
- Compare Phones
Latest Gadgets
- Realme Note 80
- Vivo V70 FE
- Realme C83 5G
- Nothing Phone 4a Pro
- Infinix Note 60 Ultra
- Nothing Phone 4a
- Honor 600 Lite
- Nubia Neo 5 GT
- MacBook Neo
- MacBook Pro 16-Inch (M5 Max, 2026)
- Tecno Megapad 2
- Apple iPad Air 13-Inch (2026) Wi-Fi + Cellular
- Tecno Watch GT 1S
- Huawei Watch GT Runner 2
- Xiaomi QLED TV X Pro 75
- Haier H5E Series
- Asus ROG Ally
- Nintendo Switch Lite
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAID5BN-INV)
- Haier 1.6 Ton 5 Star Inverter Split AC (HSU19G-MZAIM5BN-INV)
© Copyright Red Pixels Ventures Limited 2026. All rights reserved.

















